Information Is Currency
Before we jump into the electromagnetic (also know as EM) side of things, I would like to make a few brief comments about the things people, organizations, and governments feel have value since the birth of the Internet. Since recorded history, humans have named the Ages after the things that were the most valuable at the time: Stone, Bronze, Iron, and now Information Age.
This is not a mistake, though many modern humans are oblivious to the fact of how powerful the label of the era is. If you have the right information at the right time, you can live comfortably for the rest of your life. There is a specific reason why military operations centers, businesses, stock markets, why they all funnel information to the center of their decision-making cortex. Because it is valuable.
If you stop and look around you for a moment, you are immersed in it. In fact, you really can't escape it. If you disconnect yourself from the grid and live in the most remote place you can possibly find, you will still want to know what the weather will be like tomorrow; you will still need information.
Hackers (and I can't express to you how much the connotations of that word make me gag) are adept at gathering, filtering, processing, and acting on information. From the most noob-tastic script kiddie, to the most dangerously elite or benevolent of us, there is an insatiable internal propellant that feeds on the digestion and beneficial products of information. So much so, that unlike the contracted government employee, if you give a dedicated person a reason they will pick through your life for months late into the night and crunch every bit of traffic and spat of metadata you produce, just to glean information from you. But the true hacker only wants to know how things work, test the boundaries of systems and devices, and build on the things they learn along the way. They are progressing in their skillset as long as they are doing something to learn.
The companies people work for are an even more delicious target. Not because of the monetary assets they control, but because of the precious information they store. That's why very few companies say "oh bollocks, the hackers transferred $50 million from our primary account" in the news. It's always information, connected to people, where the most lucrative heists are successful. The reason why is, to be frank, $50 million dollars is only $50 million dollars. A victim's identity, their medical records, their credit information, and the information to create fraudulent accounts is immeasurably valuable.
The reason I wanted to bring this up is because I believe there are two ways to become a seasoned hacker: one is through the study of computers; the other is through the study of electromagnetism. The most well-rounded path is to study both at the same time, because they're based on the same principles. Most choose the computer path, because who wants to build an antenna garden in their back yard? Well, me.
The purpose of this article is to show interestingly striking comparisons between both fields, and to show you that you are probably smarter than you think you are. Most of all, this article was written to help you protect yourself from the nefarious actors that want your information.
If there is a God or a higher power, their design of the universe was based on copy-cat physics concepts. Once you learn one model of explaining the invisible waves and packets of data that zip down cable lines, the rest of them fall in to perfect place, simply. So we're going to dive in from the very smallest of concepts, and by the last installment you will have an expert understanding of how to catch invisible information and make it yours. You will also know how to secure your information, your family's information, the signals that come from your home, and how make these transmissions more costly to hacker in their time and money to hijack than your information is worth.
This will be a several part series under the name Electronic Education. The beginning articles will consist of some terms and definitions, and we will build on them until by the end of the series you will be able to build your own WiFi cantenna, explain how Stinger technology works, and be able to explain how a Tempest system can foil even the most stringent and classified electronic protection methods devised by the United States government.
So let's begin.
The "Wind" of Information
Electromagnetic waves are all around us, all the time. It is impossible to completely escape them, no matter where you go on Earth or in the universe. They are mostly invisible to us; trying to explain what they look like in explicit detail would be much like you holding up a family photo to your WiFi router. Your router has no idea what those photons bouncing off the photo paper mean, and it certainly can't assign any meaningful value to what your mother dressed in denim in the photo means to you (or what it meant to you when she submitted that photo along with her congratulations to the yearbook club your senior year). The device only understands a specific portion of the electromagnetic spectrum.
To explain, let's talk about some antennas you've naturally developed already that can be used to explain how other electromagnetic devices work. Your eyes, your ears, and your nervous system in general can all be considered a type of "antenna" that interacts with electromagnetic fields.
Take a minute to look at your surroundings and take note of every color you see. Photons, or light waves, bounce and scatter at different frequencies off every surface you can see. Your eye and brain interpret these different photon frequencies as color, shade, depth, and form.

Now quiet your mind and listen to the sounds around you. You may hear a fan in the background (because it's hot in here), birds chirping, your children yelling, etc. These vibrations in the air are funneled down your external acoustic meatus (your ear hole), into complex organs in your ear. These vibrations in the air vibrate tiny cilia within your ear, and your brain developed to interpret them as sound. Says something, anything. Say "cellar door" or "I will click on advertisements on this website." Your vocal cords vibrate the air, and even though the fan might not respond to you, your children might. Again, another set of biological antennas connected to your body. While sound is included in the electomagnetic spectrum, I feel that it is loosely defined as electromagnetic energy, since it is only air molecules that vibrate instead of anything specifically electronic or magnetic.
Artist credit: Yuumei
Through leaps in technology within the last century or so, humans have developed electronic "ears", "vocal cords", and "eyes" that are sensitive enough to speak and listen on frequencies that are outside of the range of human perception. Your Wifi modem speaks and hears on the 2.4 GHz and 5 GHz frequencies on the electromagnetic spectrum (I know for many of you, that might not mean much yet, but we're getting there). Your Xbox and PS4 controllers also speak and hear on the 2.4 GHz frequency. AM radio speaks from 153 kHz up to 26.1 MHz, depending on which country you're in.
Those numbers might not mean anything to you yet, but just realize that EM energy is flying around you in multiple directions at the speed of light, all the time. This is what I call the "Wind of Information" because if you build the correct sail, you can catch a lot of it. Much of the information doesn't only have to do with wireless technologies, but wired as well. If you understand how all of it works, nothing electronic will ever be a mystery to you.
James Clerk Maxwell published a set of mathematical equations between 1861 and 1862 that form the basic foundation of electrodynamics. Whether you knew it or not, his work is the basis on which modern electronics, radio technology, optics, and many other communications technologies. Some of his equations describe the interactions and similarities between magnetic and electrical fields. Some of his other equations, simplified as much I dare to teach the more inquisitive of my students, prove these eloquent truths:
- A changing magnetic field will induce an electric field.
- Conversely, a changing electrical field induces a magnetic field.
If we take that concept just a stretch further, we can say that if you apply an electric current to a conductor (any electrically conductive material, such as a wire), it will produce an electromagnetic field around the conductor. Conversely, if we place a conductor within one of these electromagnetic fields, it will produce electric current on the conductor. This is the foundation upon which wireless energy transmission and reception technologies are built.
It wasn't until 1888 when Heinrich Rudolph Hertz, a German physicist came along, that Maxwell's equations were conclusively proven. Hertz was conducting experiments with spark gap generators in his laboratory. He noticed that when he energized one of the generators, it would create a spark in another, non-powered generator across the room. He was able to recreate the effect to study it, which happened to be the first time wireless energy transfer was able to be shown consistently. Hertz didn't understand the incredible importance of his discovery. When asked by his students he demonstrated the effect to, what the discovery might mean, he is quoted saying:
"I fuggin' don't know. Nothing."
Image courtesy of Robert Krewaldt.
Later, after the technology is commercialized, it is upon Hertz's concepts that the first radio telegraphs are built. The first trans-Atlantic radio broadcast took place on December 12, 1901, pioneered by Guglielmo Marconi. The technology evolved during both World Wars, along with mechanical and electronic encryption methods. Modern radio signals are used for intermittent cellular telephone conversations, and through WiFi routers to study pornography.
Before we can gain an advanced understanding of electronic signals, we have to have a common language to express a basic framework on which these technologies are built. Let's dig just a bit deeper by going over some common terms.
Fundamental Electromagnetic Terms
Electromagnetic (EM) Waves - Electromagnetic waves which are broadcast through space. These waves travel near the surface of the earth and also radiate skyward at various angles to the surface of the earth. Remember, we're talking about all EM waves in this definition. Your cellphone and WiFi router are included, but only make up a small portion of the spectrum we're going to talk about. This picture was made by the Army and taken from one of their manuals, which is why it is garbage in explaining the infinite complexity of our subject:
Wavelength - (This is the where EM hackering begins) Wavelength is the distance a radio wave travels in the time required to complete one cycle. Wait, what? What could that possibly have to do with hacking?
Well, human-manufactured electronic antennas have interesting properties. Have you ever pulled a WiFi router out of the box, and then been forced to staple gun 140 feet of antenna wire to the outside of your house like lights for Christmas? When you bought your most recent cellphone, did it come with a box of wire you had to string out to text your bae? No, you never have.
You haven't, not only because manufacturers wanted WiFi and cellphones to be convenient, but also because of the frequencies they operate on. Wavelength is determined by the frequencies on which our devices communicate.
The next term will help explain wavelength a bit more, because these two terms are bound together by physics and electrodynamic theory:
Frequency: The rate at which a process repeats itself or the number of complete cycles per unit of time.
When we're talking about electromagnetic frequencies, the unit of time will always be one second. They make it sound so complicated by measuring things "per unit of time." But with electronic radio transmissions, the measurement will always be one second.
A 2 Hz wave, or 2 cycles per second.
So, if I have a 1 Hertz (Hz) wave, that means the wave completely cycles in one second. Now, this is easy to understand if you have had any experience with a computer, at all. Let me throw this chart out really quick, just so we have some context:
Based on this chart that means your WiFi router, your Xbox, and your PS4 controller generates 2.4 billion cycles per second.
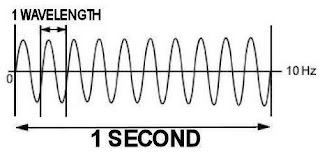
Welcome to the 21st Century, where people can build that kind of stuff on such a scale that it sits in your living room, unappreciated. That's how sensitive modern antennas are. Equipment that my cable company gives me for free can sense 2.4 billion electronic vibrations a second coming from your living room, and transmit your pornography collection, all because of advancements in modern electronics. Here is another picture to help demonstrate what a 10 Hz wave would look like. Notice how much smaller the wavelength is when the frequency gets bumped up times five:
If you compare the 2 Hz and the 10 Hz image, you'll notice the wavelength for the 2 Hz is much longer, and the 10 Hz is much shorter. You might have guessed it already:
- The lower the frequency, the longer the wavelength (and thus, the antenna used to talk with those devices).
- The higher the frequency, the shorter the wavelength (and thus, a smaller antenna is used to communicate on those frequencies).
Using sound as an example, tweeters are smaller than subwoofers for a reason. Tweeters generate sounds in a higher frequency (Mariah Carey hitting those high notes) as opposed to subwoofers generating sounds in a lower frequency (a Dubstep artist hitting a nasty drop).
Using antennas as examples, there is a reason why this sits in your phone and operates up to the GHz range:
Cellular Telephone Antenna: operates from 850 - 2100 MHz
And this operates in the kHz to MHz range, and takes up the space of a corn field:
Commercial AM Radio Tower: 0.535 - 1.605 MHz
Electromagnetic Spectrum - Imagine trying out for a rock band or symphony orchestra and when you show up to the audition, the manager doesn't know any names of any instruments and doesn't use adjectives to describe the pitch of the instruments. As the manager introduces you to the band members, you meet a guy that plays the "plucky twanger" and a lady that says she has "over ten years of experience playing the flippy-doop dapple."
The importance of that thought experiment is, if you want to speak intelligently about electromagnetism you need to know what each frequency band (or instrument in that example) is capable of. If you don't have the same common knowledge as all the other super-nerds out there, those FCC stickers on all your electronic devices don't have any useful meaning. No one can build useful hardware to talk to WiFi, cellphones, or garage door opening equipment if you don't know what frequencies it uses to talk to external devices.
The Electromagnetic Spectrum is the range of frequencies of electromagnetic radiation as measured from 0 Hertz to infinity Hertz. The electromagnetic spectrum is broken down into bands. These bands include Gamma Rays, X-Rays, visible light, audible sound, and microwaves, in addition to describing radio frequencies.
The EM Spectrum organizes frequencies into frequency bands, or ranges of frequencies between two limiting frequencies, so they can be referred to in a logical fashion. Just like musical instruments, each frequency band is useful for different functions and has its own unique properties determined by where it falls on the EM Spectrum. The following is a graphic of the EM frequency band allocations in the United States in 2003:
Click here for higher resolution.
Frequencies can be considered a natural resource. Based on technology, at any given time there are a limited number of frequencies that can be allocated. The buying, selling, and leasing of frequencies in the United States is administered by the Federal Communications Commission (FCC). The following chart is a more simplified example of some of the general frequency bands and their ITU (International Telecommunication Union) designations (i.e. VHF, UHF, etc.):
Depending on which country you're in or which textbook you reference, this chart is more-or-less the general gist of where the standard frequency bands fall. For example, some companies and textbooks insist UHF begins at 225 MHz, which is fine, except they aren't the ITU. Each frequency band (and even their sub-bands) have diverse properties and characteristics; some work better when utilized with a particular technology, while others are better suited to carry signals for other types of products and equipment. A quick overview of some of their naturally occurring uses and technologies that utilize each band:
- Very Low Frequency (VLF) - Frequency Band: 3 - 30 kHz - Wavelengths: 100 to 10 kilometers - Used for radio navigation and government radio timing signals. A characteristic of this band is its ability to penetrate approximately 40 meters through saltwater, which is why it is also used for some types of submarine communications. Because VLF has such a long wavelength it isn't often obstructed by mountains or other terrain, making it ideal for long range ground-based timing signals. This frequency band can also be refracted by the ionosphere (more on the ionosphere in a moment). (R) (D)
- Low Frequency (LF) - Frequency Band: 30 - 300 kHz - Wavelengths: 10 to 1 kilometer - Utilized for aircraft beacons, navigation, weather systems, consumer radio clocks, and AM radio broadcasts in some parts of the world. Frequencies in this band can penetrate saltwater approximately 200 meters, making it ideal for military submarine communications. This band can also be refracted by the ionosphere, as well as diffracted over and around obstacles like mountains. (R) (D)
- Medium Frequency (MF) - Frequency Band: 300 kHz - 3 MHz - Wavelengths: 1000 to 100 meters - MF is utilized for AM radio broadcasting, navigational radio beacons, and ship-to-shore communications. This band also experiences refraction and diffraction. (R) (D)
- High Frequency (HF) - Frequency Band: 3 - 30 MHz - Wavelengths: 100 to 10 meters - HF is used for aviation communication, government time stations, weather stations, amateur (HAM) radio, and citizens band (CB) radio. If you take a look at HF's wavelengths and pair its relatively manageable antenna lengths with the band's ability to (most of the time) reliably be refracted by the ionosphere and diffracted around obstacles, you can draw conclusions about why HF is used what it's used for. HF antenna design and understanding the properties of the ionosphere is an art form in many amateur, civilian, and military radio circles. The majority of my understanding of electronics and signals came from studying HF radio and it's associated technologies and disciplines. A little later in the column, we will discuss how the ionosphere interacts with and refracts HF waves of various wavelengths. (R) (D)
- Very High Frequency (VHF) - Frequency Band: 30 - 300 MHz - Wavelengths: 10 to 1 meter - VHF is mainly a terrestrial (Earth-bound), generally (but often farther than) line of sight (LOS) frequency band. It is utilized for FM radio, television broadcasts (analog and digital), two way land mobile radio systems, air traffic control, and long range data communications up to several miles with the use of radio modems, HAM radio, and maritime communication. The lower end of the VHF band may intermittently refract off the ionosphere, but only under favorable conditions, and not reliably enough to be used for long range communications the same way HF is. It is, however, less prone to EM noise interference than High Frequency communications. (~R)
- Ultra High Frequency (UHF) - Frequency Band: 300 MHz - 3 GHz - Wavelengths: 1 to 0.1 meters - The UHF band is used for TV broadcasting, cordless phones, wireless video game controllers, military satellite communications, and two-way radios. Most importantly for this series of articles, cellular phones, WiFi Internet connections, Bluetooth connections, and Global Positioning System (GPS) all utilize the UHF band to receive and transmit information. UHF waves are mainly line of sight (LOS) waves, are easily blocked easily by obstructions, but can have an narrow signal path when polarized correctly.
- Super High Frequency (SHF) - Frequency Band: 3 - 300 GHz - Wavelengths: 0.1 meter to 1 centimeter - SHF wavelengths fall within the microwave band, so SHF waves are sometimes called microwaves. Like their UHF cousins, because of the short wavelength of SHF waves they can be polarized into narrow beam-like signal paths. SHF waves are used in cellular telephone networks, point-to-point data linkages, wireless Local Area Networks (LANs), and for satellite communications. Some Directed Energy Weapons (DEWs) use the SHF band. Microwave ovens and many military parabolic dish data terminals fall within this frequency band. But contrary to the beliefs of some, equipment that is solely design for communications cannot amplify its signal to cause any harm to humans whatsoever if they are exposed for a short period of time (unless, ironically, if they happen to be wearing tinfoil hats).
- Extremely High Frequency (EHF) - Frequency Band: 300 GHz - 3 THz - Wavelengths: 1 centimeter to 1 millimeter - EHF waves have some interesting properties. They are commonly absorbed by the moisture in Earth's air, and scattered by air molecules themselves, and only have a range of one kilometer at best. Because they are scattered and absorbed by moisture, they are perfect for weather radar stations. They are also starting to become more commonly used in Personal Area Networks (PANs) because of their short range and therefore, frequency re-usability.
(R) denotes that the band is utilized in conjunction with ionospheric refraction.
(D) denotes that the band is commonly diffracted around obstacles.
There are several frequency bands above and below the bands I've listed. ELF, SLF, and ULF are below Very Low Frequencies (VLF) and above Extremely High Frequencies (EHF) is the beginning of the infrared light spectrum. I only listed the bands above as a starting point for someone who is interested to learn more.
Modulation - The process of changing a constant signal in order to carry information. Modulation doesn't only have to do with electromagnetism; there are many other applications. Demodulation is the process of "stripping intelligence" off of a modulated signal to produce useful information. All modems are named after the processes of these two terms; modem is an abbreviation of modulator/demodulator.
The two most recognized forms of electromagnetic modulation are Amplitude Modulation (AM) and Frequency Modulation (FM).
Carrier Wave - The radio wave produced by a transmitter when there is no modulating signal. A carrier wave has a constant amplitude and frequency. When you tune your car radio to 92.1 MHz, you are telling your radio to listen for the 92.1 MHz carrier wave. Same thing with KSL 1160 (1.160 MHz) carrier. The magic happens when the transmitting station encodes, or modulates, the carrier signal with music, or talk radio, or commercials.
Let me take a moment before we talk about some types of modulation to make a point. As I mentioned earlier that wavelength and the UHF band are going to be important in the follow-on columns, modulation is equally important. Hopefully, when you practice breaking passwords off your WiFi signal along with me, you'll be able to look up your WiFi router's technical specifications on Google. If you are, let's say, working as a network penetration tester for a company under completely legal circumstances and you come across a signal you'd like to learn more about, you won't always have the luxury of being able to profile their hardware. As we continue deeper into this electromagnetic mess, take note of these basic types of modulation, because there are more complicated industry standard ones out there. I would hate for you to configure something really innovative, but feel like the military radio operator that didn't hear anything on the range all day because they set their equipment to listen on the wrong modulation.
Amplitude Modulation - The amplitude (or voltage level, field intensity, or power level) of a carrier wave is varied above and below its normal value, in accordance with the information being encoded onto the carrier wave. The frequency of the carrier wave remains the same. Because there many naturally occurring and man-made sources of EM noise that mimic the way AM is transmitted, AM is especially susceptible to atmospheric noise. This is why AM radio typically sounds "fuzzy" on your car stereo.
Frequency Modulation - The frequency (the number of cycles per second) of a carrier wave is rapidly deviated to encode information. Because there are very few sources of Frequency Modulation in nature, FM channels tend to be very "clean" sounding. You can tell the acoustic (because of the signal type) differences between FM and AM if you switch back and forth between them on your car stereo.
There are probably very few FM .gif images available because it's not as fun to look at as AM. Image courtesy of tutorvista.com.
The follow image shows a modulating signal (this could be voice, data, or really anything) on top (blue), followed by a carrier wave (red). Next is an AM signal (green) encoded to carry information from the modulating signal. Last is a FM signal (pinkish purple) encoded to carry information from the modulating signal.
Image courtesy of lossenderosstudio.com.
Fading occurs when a signal travels over long distances. If you have ever taken a long road trip with the radio on, you have experienced this phenomenon on both AM and FM stations. Because radio signals are attenuated (or weakened) over distance, you will hear a radio station fade as you travel and pick up another one when its signal becomes stronger than the more distant station.
You also experience fading when you catch a signal after it strikes or travels through obstacles. Those of you fortunate enough to have large houses experience this in rooms that are distant from your WiFi router.
Polarization is another extremely important (and interesting) characteristic of electromagnetism. Every time any radio wave is produced, it creates two types of charged fields: an electric field, and a magnetic field. These two fields travel through the air (or space) at 90 degree angles to one another. Their shapes and forms perfectly match one another and look exactly like radio waves (because they are). These two fields propel (or propagate) one another through space, creating their forward motion.

This phenomenon is exactly the reason some "grinders" and bio-hackers choose to implant neodymium magnets into their fingertips. Once the incision heals, the sensitive nerve endings in their fingertips are able to sense the magnetic portion of radio waves from a short distance. This is useful for technician or electronic infrastructure jobs, where the bio-hacker can actually feel if a wire is live or if a magnetic hard drive is functioning (and no, it doesn't interfere with the data stored on the magnetic disk platters). It also makes a neat bar trick and is useful for frightening helicopter parents.
Video courtesy of my left ring finger.
The angles of the electromagnetic parts of radio waves can be manipulated easily, sometimes even on accident. All you have to do is move the antenna to change the propagation starting point of the EM waves and you have successfully modified their polarization. Back when television was more commonly broadcast over radio signals, each TV set came with an antenna. I have heard of fathers instructing their kids to "go mess with those damn rabbit ears on the TV so I can watch the game." What he was actually telling you to do was "go modify the receptive polarization of that damn vee antenna so it matches the polarization of the transmitting television station's propagating electric field." Yes, many of you were antenna engineers by the time you were five and you didn't know it.
Like your Dad said in the previous paragraph, a radio antenna's polarization is referred to by the direction of the electrically charged field in relation to the surface of the Earth. Antennas that stick straight up in the air are considered vertically polarized. Vertically polarized antennas tend to have an omni-directional propagation pattern, which means that signal is transmitted and received equally in all directions from the antenna.
Top photograph courtesy of zerofive-antennas.com
Antennas that run parallel to the ground are known as horizontally polarized antennas. These generally have a bi-directional propagation pattern, meaning they transmit and receive radio signals equally in only two directions.
Dipole Antenna, credit: Loodog
Antennas that are arranged at 45 degree angles to the Earth's surface, or have both vertical and horizontal elements (or wires) have mixed polarization. Mixed polarization is useful is you want to receive both horizontal and vertical signals at the same time, but it doesn't receive either type of polarization exceptionally well.
It is certainly possible for a vertical antenna to receive a signal from a horizontally polarized antenna, but then you run into what's called polarization mismatch. To demonstrate the point, imagine that a train traveling down some straight tracks is a radio wave traveling through space. You need to build a space to receive as much of the train (or radio wave) as possible, like a train tunnel. There is a reason train tunnels are built tall and slender (vertically), and not short and wide (horizontally). If you built a train tunnel short and wide, I'm sure some parts of the train would make it through to the other side, but it wouldn't be pretty.
The same thing happens with polarization mismatch; you want to orient your antenna to catch as much signal as possible by matching your antenna's polarization with the transmitter's antenna.
The last type of polarization we're going to discuss is circular or elliptical polarization. All satellites I know of, as well as the satellite dishes that receive them are circularly polarized. If you take a look at the red and blue electromagnetic diagram again, then imagine as the wave travels through space as it changes phase every four cycles. The diagram above shows just a regular horizontally or vertically polarized wave, but one that shifts 90 degrees every time it completes one cycle, completes one "phase" every four cycles. If that's too much to fathom (it is for me, because I have trouble thinking in 4 dimensions), the diagram below simplifies the concept a bit:
Credit: Dave3457
When the DirectTV guy "installs" your dish, all he does is affix it to a sturdy surface and adjusts the polarization to catch the signal coming from the satellite in space. If you pay the "technician" any amount of money, know that you could have probably installed it by yourself on accident. Also, cable television is a terrible waste of your time and money.
In the Next Section
We are going to discuss just a bit more about important influences on electromagnetic energy, use examples of HF waves interacting with the ionosphere to demonstrate some of the more interesting properties of radio waves, talk about ideal locations for antennas, and basic types of antennas. Then we will get into encryption, the different languages machines use to talk to one another (including binary), how that information is transmitted and received, and how you can learn to listen in on some of it.